With over 80% of websites powered by PHP, it is one of the most common languages for website development. Developers spend hours writing codes, but PHP security issues and bugs inadvertently creep in and make the entire website vulnerable to cyberattacks. During the development phase, common security practices might get easily overlooked making the website susceptible to cybercriminals.
With this guide, I hope to educate you on some PHP security issues and quick steps to fix them. Read on to find out how you can protect your website from most cyberattacks. A complete professional security audit will be a great approach to find all vulnerabilities in your site & find ways to patch them.
1. SQL Injection
One of the most common methods of attack is SQL Injection works by injecting SQL queries into websites or applications that are linked to databases.
In this attack, with the use of specially crafted queries, attackers can access your database and perform actions such as modifying or deleting data. It is also used to steal sensitive information from a website leading to credential theft or data leaks.
Fix:
SQL Injection can be stopped by simply validating input data entered into the website. Input data must be cleaned and sanitized before it is executed within the application. Steps such as validating JSON and XML schemas, minimum and maximum limits for numerical input including dates, whitelisting characters, and managing regular expressions, to name a few, will help you tackle this type of attack and solve PHP security issues.
2. Remote Code Execution and Malicious File Inclusion
In this, attackers remotely take control of an application by running malicious scripts, which also include tricking the application into downloading harmful files further infecting the system. Multiple reasons cause this vulnerability, but the most common is the misuse of “include” and “require” functions.
Fix:
Initialize all variables properly and switch OFF the register_globals directive. Also, regularly update plugins and other applications with the latest security patches. Managing appropriate user permission also helps in minimizing the damage by limiting the access of an attacker.
3. Cross-site scripting (XSS) attacks
One of the most common PHP security issues, the objective of a Cross-Site Scripting attack (XSS) is to insert harmful HTML or JavaScript into the application to perform a range of tasks. This risk often happens when input is not sanitized, among other reasons. XSS also allows the attacker to steal cookies, install keyloggers, and take control of the user’s browser, to name a few.
Fix:
XSS attacks can be avoided by encoding certain wildcard characters into HTML entities. Websites should strictly filter all input data and encode the output data to not interpret it as active content. Also, use suitable response headers, such as “x-content-type-options” headers to make sure that the browser correctly interprets the HTTP responses. Such attacks can lead to redirection, SEO Spam, or even to complete compromise of the site or store.
4. Session Hijacking
Session hijacking is one of those PHP security issues that put the users’ accounts in the crosshair. Through cookie theft, attackers can hijack sessions of unsuspecting users and end up impersonating them to gain access to the application. Once an attacker gets access to a user account, they can misuse their permissions and privileges.
Fix:
To prevent session hijacking, use “session_regenerate_id()” methods to keep changing the session IDs. This will ensure that even if a session ID is stolen it will become invalid after a short time. Also, store all user credentials in a secure location in an encrypted format. Allowing login and password change pages to be accessed through SSL is often a good idea.
5. Directory traversal attacks
In this vulnerability, third-party users can access admin files and folders beyond the root folder. With access to core files, attackers can compromise the application by altering or deleting those files. Directory traversal attacks can be launched either through browsers or website portals.
Fix:
Such types of attacks can be stopped by taking basic precautions such as sanitizing inputs, managing user permissions, and changing default paths of admin files and folders. You can try to store an encrypted version of the files in a separate location.
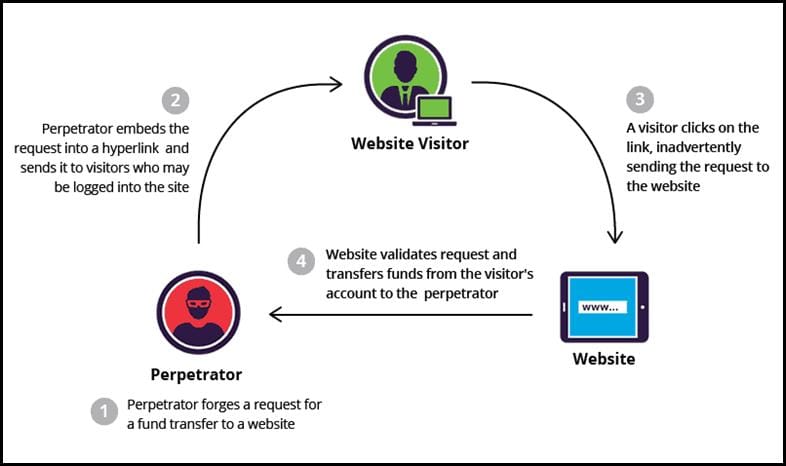
6. Cross-Site Request Forgery Attack (CSRF)
In CSRF, the attacker tries to make the administrator click on a link that performs a malicious task. Once the site administrator clicks on the link, the attacker can get access through admin privileges and take over the application. CSRF is generally used to change the state of the application such as by updating credentials or user access privileges.
Fix:
Such types of PHP issues can be prevented by introducing anti-CSRF tokens, which are random strings that are stored within session variables. “SameSite Flag” cookies ensure that only identical domains can make POST requests and block requests originating from other domains that might be potentially harmful.
Final Words
Resolving PHP security issues is necessary to keep your web application safe from attackers. Risks, as shown above, can be mitigated by taking basic security measures and with a mindset of making PHP security a foundation of the application.
However, even after taking all precautions, there are chances that security bugs might be present. To sniff out such vulnerabilities, you need a security expert in the field. Through a professional VAPT and with more than 1500 tests, security experts find out all security vulnerabilities in your website/application. You will also get the necessary assistance in fixing those security gaps and will secure your website for the better.